

It is quite evident that rapid increase in billions of IoT devices has already created a weak spot in the ecosystem due to lack of security. With more and more devices getting connected, the biggest challenge is to secure them. These devices are easy targets for hackers who look to gain control and access the device, network, and cloud, and eventually stealing user’s data. So, for an IoT device to be secured, the hardware, software, and connectivity needs to be secured too.
Now the question arises, what is the best method to implement IoT Security? The solution for this is adopting Security by Design approach. Security by Design states that every IoT system’s initial design process should start with security. This means security should be built into IoT hardware and Software from the beginning itself and not at later point of time after the IoT device is being hacked or compromised.
Every IoT Developer or Project Architect should ensure that the IoT device identity is strong, remains unique and tamper resistant. Developer should be able to create Root of Trust (RoT) within the system so that whole system is secured. RoT is the fundamental security component of any connected IoT device. It is an implementation of group of trusted functions, which the device can use to ensure security. This can be realized through Software and Hardware implementation.
The software/firmware implementing its specific functionality must be integrity-protected. In the case of an IoT device with sensor, a chain of trust must be established from the sensor to the microcontroller and wireless module, and all the way through to the end application. In general, we should follow five pillars architecture for a secure IoT design as given below. One of the largest IOT module sellers, Ublox, follows the below Security architecture in their IOT modules.
Another level of IoT security is at Hardware level. Adding protection at the silicon level is one of the best ways to shield a device with necessary defences.
ARM is providing Hardware security support through TrustZone for Cortex-A and Cortex-M series SoC with Armv8-M instruction set. So, developer should choose SoC based on the criticality of the final application and also development tools like ARM Keil will add security features like Public and Private Keys for the project builds.
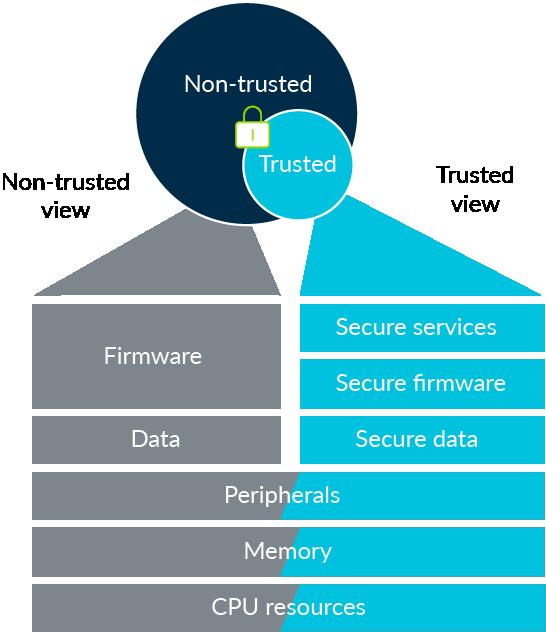
Silicon is the heart of the device and a strong foundation on which a device can be built. The protection of device identities in IoT requires specific hardware support in order to isolate them from the multiple software layers. These layers keep changing during multiple software updates to prevent remote extraction or local leakage independently from the device software, or counter unauthorized modifications by a compromised software. The keys used to verify software executed on an IoT device must be securely provisioned onto the hardware. These keys should also be integrity-protected, independently from the software. They are supposed to verify and load at different stages of the device lifecycle, at manufacturing or Over the Air (OTA) in the field.
Silicon is trustworthy as it is highly stable and resistant to change. The starting point for this hierarchy of security, that is, the base that supports the layers of abstraction, is known as the root of trust. The root of trust is something that is inherently trustworthy. The right root of trust creates a firm foundation for security. While the lines of code, data stored in memories, operating systems and user interfaces are relatively easy to alter or damage, physically isolated programs and data in silicon and data kept in an immutable silicon are highly stable and resistant to change.
So, Hardware security is the proprietary for the SoC vendor. Most of the vendors are introducing Security at hardware in their portfolio. For instance, NXP is providing Secure Element as Hardware security in addition to the ARM TrustZone shown in the below Fig 2. So, developers have options to choose based on the criticality of the IoT system development.
This way, to avoid security breaches, IoT device makers and developers should employ different approaches to protect the device from being accessed by anyone through the Internet and not becoming easy targets for hacking.